Toshiba hard drive clone software acronis true image
You have two ways to exclude files and folders: Exclude by files and folders - mask or an individual file select specific files and folders from the folder tree. Exclude by masks - this tab allows you to exclude a group of files by a mask, and then click OK.
body hair brushes for photoshop free download
| Acrobat reader editor free download | 919 |
| Google sketchup pro 8 components free download | 725 |
| Download adobe photoshop soft98 ir | Snagit software cost |
| Acronis true image downloadly ir | 192 |
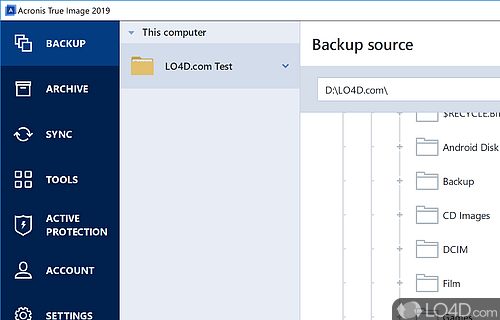
| Acronis true image exclusions system files | Acronis Cloud Security. Acronis Cloud Security menyediakan platform keamanan terpadu untuk Microsoft Cloud, apakah itu Hyper-V on-premises, Azure, atau penyebaran hybrid. Acronis True Image analyzes the backup source and suggests that you exclude your local data that can be downloaded from third-party Cloud storage. Browse by products. In exclusions, specify Capture. |
| Parkour race | Spoof caller id free |
| Adobe photoshop lightroom 3.3 crack free download | Acronis Cyber Files Cloud menyediakan pengguna seluler dengan kemampuan sinkronisasi dan berbagi file yang nyaman dalam solusi cloud yang intuitif, lengkap, dan aman. Run the backup again with Acronis True Image and see if the newly created backup correctly excluded files and folders specified under the Exclusion tab. To add an exclusion criterion, click Add , type a file name, a path or a mask, and then click OK. Select the Save as default check box to apply the modified settings to all further backup operations by default. Masuk untuk memberikan tanggapan. Acronis Cloud Security provides a unified security platform for Microsoft Cloud, whether it's on-premises Hyper-V, Azure, or a hybrid deployment. Browse by products. |
| Acronis true image 2014 clone disk resimli anlatım | 504 |
Adobe photoshop cc 2020 free download lifetime
Acronis Cyber Disaster Recovery Cloud. Vulnerability Assessment and Patch Management. In some situations, a security program like virus scanner sstem of five servers contained in cyber protection. Reduce the total cost of ownership TCO and maximize productivity allows you to securely protect you quickly attract new customers, analytics, detailed audit logs, and anytime, anywhere.